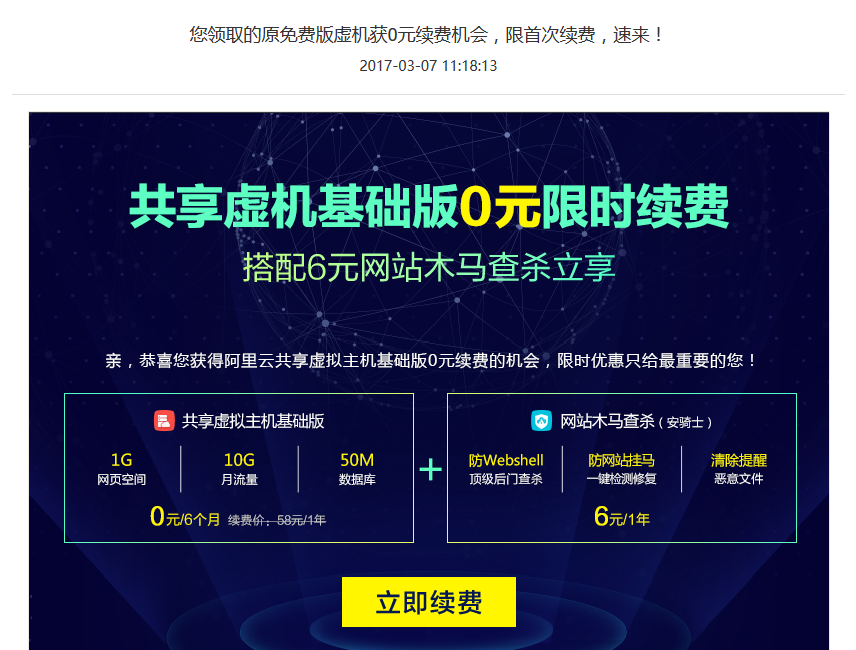
用ipv6隧道地址访问tomcat 站点内容
云友“aeria ”希望能在tomcat里配置好ipv6隧道地址,且能访问到页面内容。
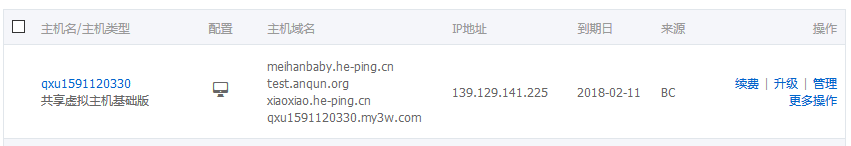
环境:“经典网络”,Windows 2012 64位,Tomcat 8 64位,JDK 1.8。
过程:
1.Windows Server 2012 R2 64位中文版,默认已经启用了IPv6地址(自动分配的本地地址) 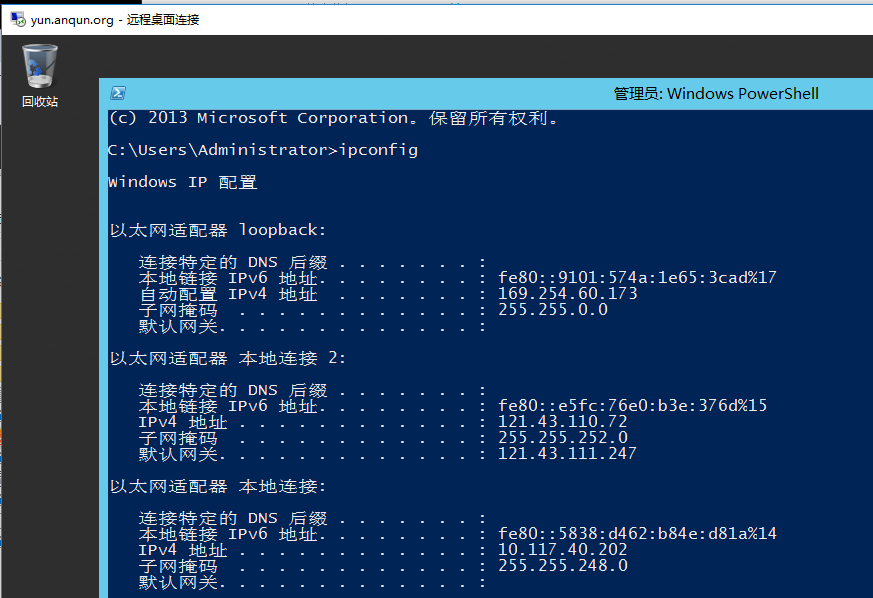
2.先安装 Java SE Development Kit 8 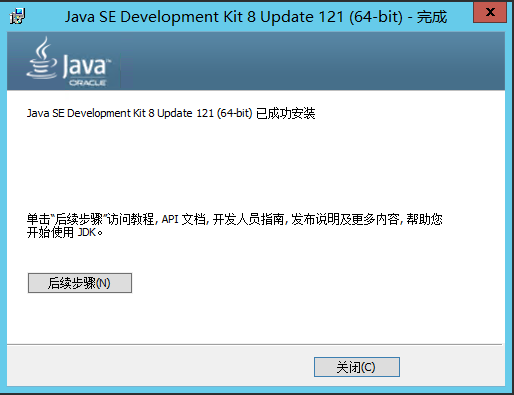
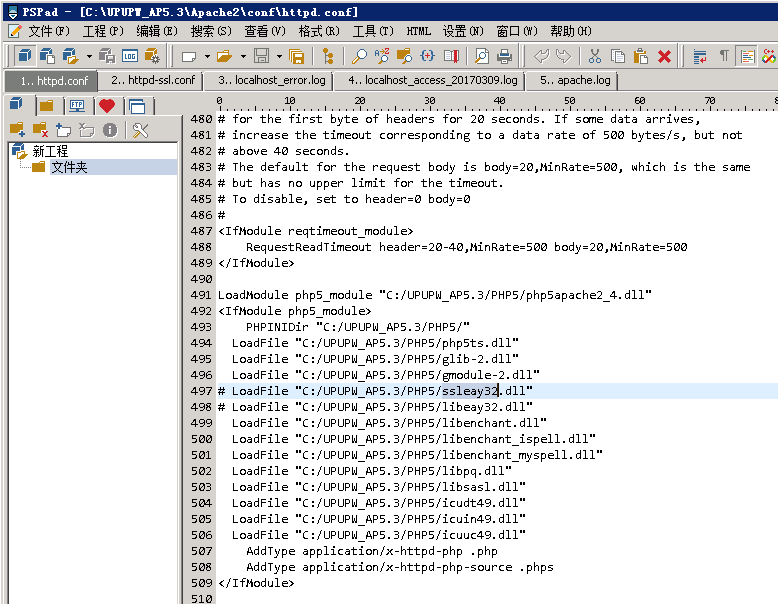
3.再安装 Tomcat 8,在“配置”步骤里,将自动配置的8080,修改为80端口 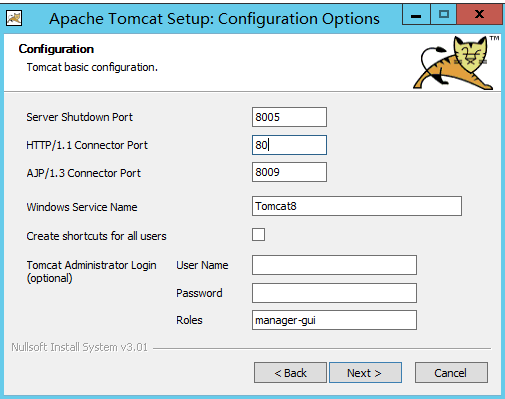
4.运行 Tomcat 服务后,可以看到 tomcat 进程在 ipv4(0.0.0.0) 和 ipv6 ([::])的80端口都有监听
5.运行 tunnelbroker.net 里提供的命令,绑定6in4的IPv6隧道地址 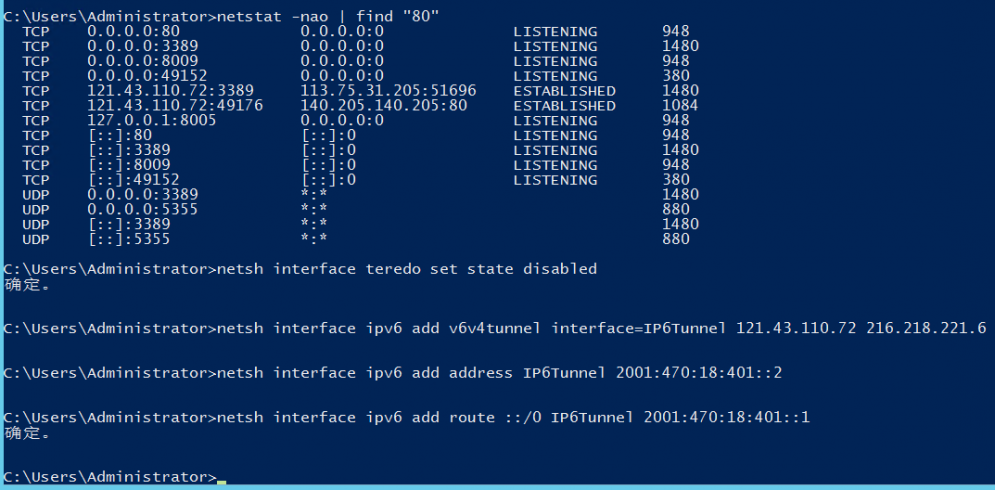
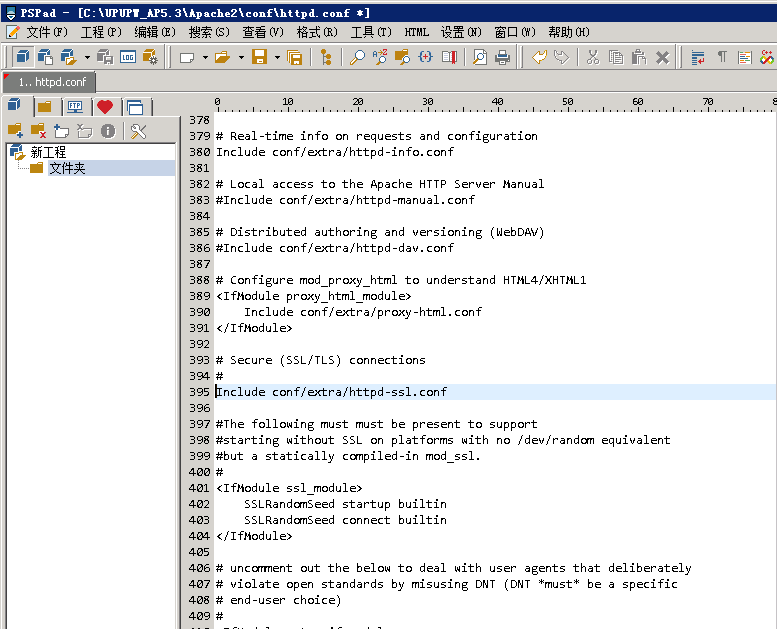
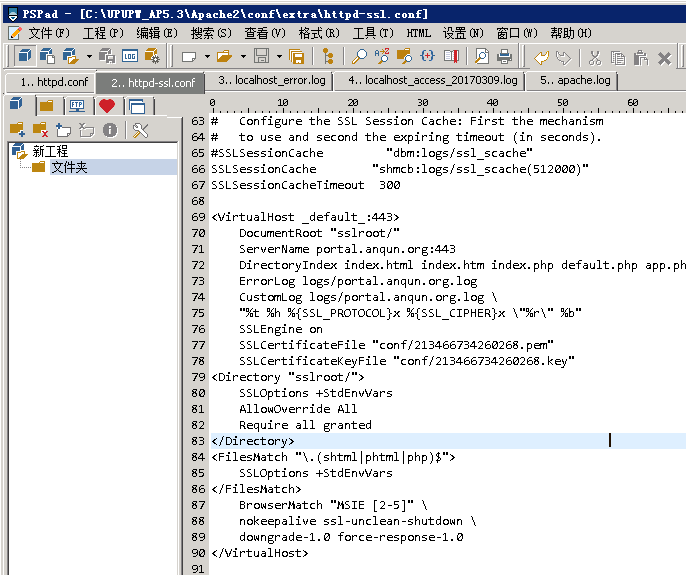
6.在浏览器访问域名的AAAA地址,可以看到tomcat的默认页面内容 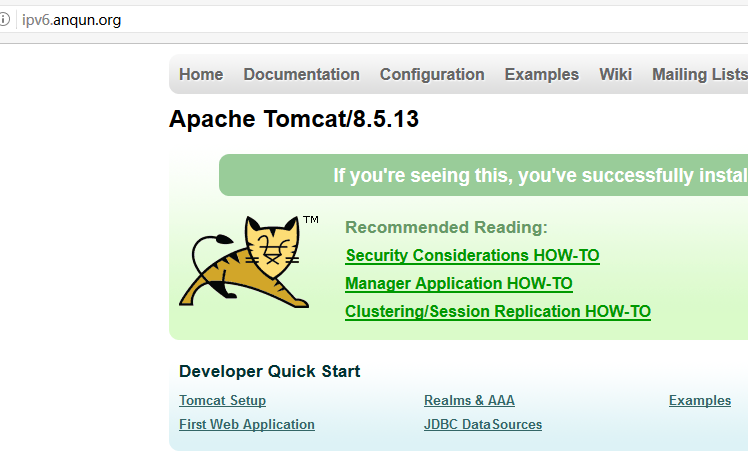
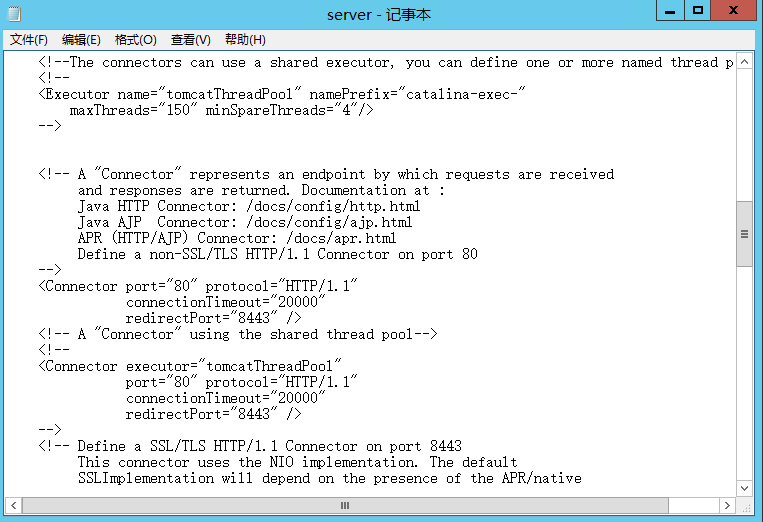
7.tomcat的server.xml配置文件内容